If you have already created a SPN for the SSO via Microsoft you can reuse this SPN for the connection to SharePoint. This makes particular sense if you do not plan to create multiple SPNs for different SharePoint sites.
- Creating an App Registration in Microsoft Entra ID to generate the required credentials.
- Configuring API Permissions to define what the application is allowed to do.
- Granting Access to Specific SharePoint Sites to connect the SPN to the data.
- Client ID (Application ID)
- Tenant ID (Directory ID)
- Client Secret (Application Password)
Part 1: Create the App Registration and Credentials
First, you need to register a new application in your Microsoft Entra ID portal. This registration represents the identity of our service within your Microsoft environment.-
Navigate to App Registrations:
- Log in to the Microsoft Entra admin center.
- In the left-hand navigation pane, go to Identity > Applications > App registrations.
-
Create a New Registration:
- Click
+ New registration. - Give the application a descriptive name, such as “SharePoint Integration Service”.
- Leave the other settings at their default values and click Register.
- Click
-
Save the Client ID and Tenant ID:
- Once the app is created, you will be taken to its Overview page.
- Copy the Application (client) ID and the Directory (tenant) ID. Save them in a secure location, as you will need them to configure the integration in our platform.
-
Create a Client Secret:
- In the navigation for your app registration, go to Certificates & secrets.
- Click on the Client secrets tab and select
+ New client secret. - Provide a description (e.g., “SharePoint API Key”) and choose an expiration period.
- Click Add.
Part 2: Configure API Permissions
Next, you must specify the exact permissions the application needs. We will use theSites.Selected permission, which follows the principle of least privilege by allowing you to grant access only to specific SharePoint sites instead of all of them.
- Go to API Permissions:
- In your app registration’s navigation menu, select API permissions.
- Add a Permission:
- Click + Add a permission and select Microsoft Graph.
- Select Application Permissions:
- Choose Application permissions. This type is required for services that run in the background without a signed-in user.
- Add Sites.Selected Permission:
- In the “Select permissions” search box, type
Sites.Selected. - Check the box next to Sites.Selected under the “Sites” category and click Add permissions.
- In the “Select permissions” search box, type
- Grant Admin Consent:
- The newly added permission will have a status indicating that admin consent is required.
- Click the Grant admin consent for [Your Tenant Name] button at the top of the permissions list.
- Click Yes to confirm. The status should now update to show a green checkmark, meaning the permissions are active at the tenant level.
Part 3: Grant Access to SharePoint Sites
The final step is to grant the newly created SPN access to each SharePoint site it needs to read. This process must be repeated for every top-level SharePoint site that you intend to use with our service. You can either do this via Fivetran or via the PowerShell. We would recommend using Fivetran, as it is much easier - you can find the needed steps in the following section. Credits and further description here.1
Grant access for a selected site to the SharePoint app
-
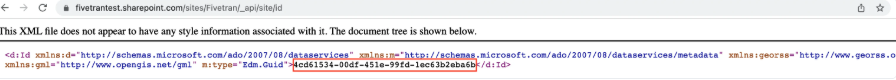
Navigate to the site you would like to connect to Fivetran > Home > Append /_api/site/id to the site’s URL in your browser.

- Make a note of the site ID in the JSON response as shown below. You will require this site ID in further steps.
- Sign in to Microsoft Graph Explorer with an account that has a SharePoint Administrator or higher role.
- In Graph Explorer, on the top right, click your avatar.
- Select Consent to permissions (by clicking on the “Modify Permissions” tab - see screenshot below) and then choose Consent for Sites.FullControl.All to provide the Graph Explorer tool the ability to modify site permissions for your tenant.
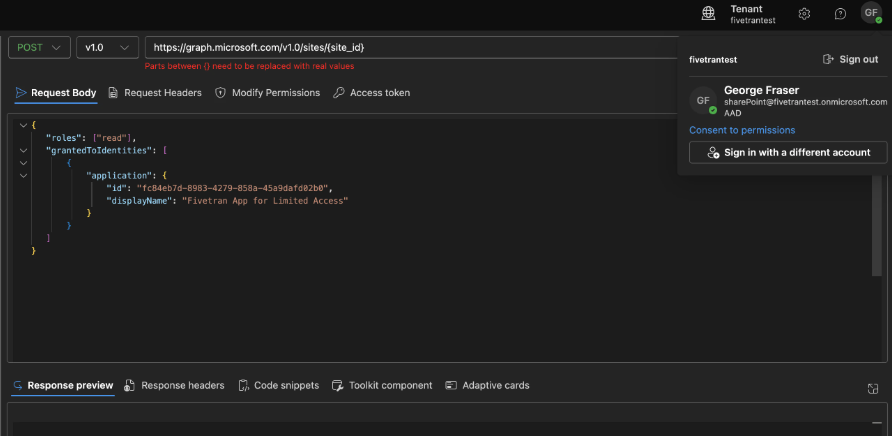
- Make a POST request to the endpoint
https://graph.microsoft.com/v1.0/sites/{site_id}/permissionswith Request HeaderContent-Type: application/jsonand Request Body:
body
2
Select Site ID
Depending on the access type you selected, perform the following steps:Quick setup (All sites via Fivetran App)
- Click Authorize. You will be redirected to your SharePoint account to authorize Fivetran’s access. Once you have finished, you will be redirected back to Fivetran.
- Set the Use Input Field for Site toggle to choose how you want to specify the SharePoint site:
- If the toggle is set to ON, a text input field appears, allowing you to manually enter the site using the format hostname,siteCollectionId,siteId.
- If the toggle is set to OFF, use the Sync Lists from Site drop-down menu to select the SharePoint site from the available list.
- In the Connect section, enter the Tenant ID, Client ID, and Client Secret you found.
- In the Site Id field, enter the site ID that you found.
- (Optional) Click Run connection test to validate the credentials and connection to SharePoint.
3
Finish Fivetran configuration
Click Save & Test. Fivetran will take it from here and sync your data from your lists.
You have now successfully configured the SPN for one SharePoint site. Remember to repeat this “Part 3” for all other required SharePoint sites.
